※ 발췌 (excerpts):
출처 1: https://en.wikipedia.org/wiki/Trusted_timestamping
Trusted timestamping is the process of securely keeping track of the creation and modification time of a document. Security here means that no one─not even the owner of the document─should be able to change it once it has been recorded provided that the timestamper's integrity is never compromised.
The administrative aspect involves setting up a publicly available, trusted timestamp management infrastruction to collect, process and renew timestamps.
History
The idea of timestamping information is actually centuries old. For example, when Robert Hooke discovered Hooke's law in 1660, he did not want to publish it yet, but wanted to be able to claim priority. So he published the anagram ^ceiiinosssttuv^ and later published the translation ^ut tensio sic vis^ (Latin for "as is the extension, so is the force"). Similarly, Galileo first published his discovery of the phases of Venus in the anagram form.
Sir Issac Newton, in responding to questions from Leibniz in a letter in 1677, concealed the details of his "fluxional technique" with an anagram:
The foundations of these operations is evident enough, in fact; but because I cannot proceed with the explanation of it now, I have preferred to conceal it thus: 6accdae13eff7i3l9n4o4qrr4s8t12ux. On this foundation I have also tried to simplify the theories which concern the squaring of curves, and I have arrived at certain general Theorems.
Classification
( ... ... )
Trusted (digital) timestamping
According to the RFC 3161 standard, a trusted timestamp is a timestamp issued by a Trusted Third Party (TTP) acting as a Time Stamping Authority (TSA). It is issued to prove the existence of certain data before a certain point (e.g. contracts, research data, medical records, ...) without the possibility that the owner can backdate the timestamps. Multiple TSAs can be used to increase reliability and reduce vulnerability.
( ... ... )
Creating a timestamp
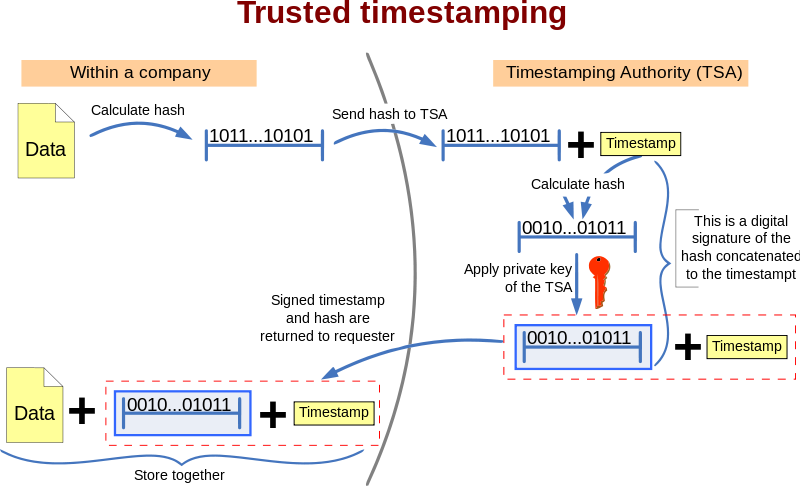
The technique is based on digital signatures and hash functions. First a hash is calculated from the data. A hash is a sort of digital fingerprint of the original data: a string of bits that is practically impossible to duplicate with any other set of data. If the original data is changed then this will result in a completely different hash. This hash is sent to the TSA. The TSA concatenates a timestamp to the hash and calculates the has of this concatenation. This hash is in turn digitally signed with the private key of the TSA. This signed hash + the timestamp is sent back to the requester of the timestamp who stores these with the original tata (see diagram).
Since the original data cannot be calculated from the hash (because the hash function is a one-way function), the TSA never gets to see the orginal data, which allows the use of this method for confidential data.
Checking the timestamp
Anyone trusting the timestamper can then verify that the documents was ^not^ created ^after^ the date that the timestamper vouches. It can also no longer be repudiated that the requester of the timestamp was in possession of the original ata at the time given by the timestamp. To prove this (see diagram) the hash{https://en.wikipedia.org/wiki/Cryptographic_hash_function} of the original data is calcualted, the timestamp given by the TSA is appended to it and the hash of the result of this concatenation is calcluated, call this hash A.
Then the digital signature of the TSA needs to be validated. This can be done by checking that the signed hash provided by the TSA was indeed signed with their private key by digital signature verification. The hash A is compared with the hash B inside the signed TSA message to confirm they are equal, proving that the timestamp and message is unaltered and was issued by the TSA. If not, then either the timestamp was altered or the timestamp was not issued by the TSA.
Decentralized timestamping on the blockchain
With the advent of cryptocurrencies like bitcoin, it has become possible to securely timestamp information in a decentralized and tamper-proof manner. Digital data can be hashed and the hash can be incorporated into a transaction stored in the blockchain, which serves as a secure proof of the exact time at which that data existed. The proof is due to a tremendous amount of computational effort performed after the hash was submitted to the blockchain. Tampering with the timestamp would also lead to breaking the integrity of the entire digital currency[4] , and this would result in the digital currency devaluing to zero.[4]
The decentralized timestamping approach using the blockchain has also found applications in other areas, such as in dashboard cameras, to secure the integrity of video files at the time of their recording, or to prove priority for creative content and ideas shared on social media platforms.
See also
- Timestamp
- Timestamping (computing)
- Cryptography
- Computer security
- Digital signature
- Digital postmark
- Smart contract
출처 2: https://en.wikipedia.org/wiki/Timestamp
A timestamp is a sequence of characters or encoded information identifying when a certain event occurred, usually giving date and time of the day, sometimes accurate to a small fraction of a second. The terms derives from rubber stamps used in offices to stamp the current date, and sometimes time, in ink on paper documents, to record when the document was received. Common example of this type of timestamping are a postmark on a letter or the "in" and "out" times on a time card.
In modern times usages of the term has expanded to refer to digital date and time information attached to digital data. For ex., computer files contain timestamps that tell when the file was last modified, and digital cameras add timestamps to the pictures they take, recording the date and time the picture was taken.
Digital timestamps
( ... ... )
출처 3: [제10강, PPT] 전자 무역, E-Trade
2. 전자 인증과 보안 인증: (가) 기밀성, (나) 인증, (다) 무결성(integrity), (라) 부인 방지(non-repudiation)
3. 인증 기관의 역할: 신분 확인, 공개키 인증, 시간 날인, 증거 확보, 배달 매가, 분쟁 해결 등
출처 4: 폐쇄형 전송 시스템에서 열차 제어 신호 전송 방법
장비의 결함에 의해 잘못된 시간에 전송 될 수 있던 것을 송신기 응용 계층에서 기본 전송 프레임에 시간 날인 필드를 추가하여 수신기 응용계층에서 이상 여부를 확인할 수 있도록 하여 안전한 통신을 달성하는 폐쇄형 전송 시스템에서 열차 제어신호 전송 방법을 제공하는 것 ( ... ... ) 기본 전송 프레임의 데이터 송신자 정보를 나타내는 출처 식별자 필드를 생성하는 단계와, 송신기 응용 계층에서 상기 기본 전송 프레임의 시간 정보를 나타내는 시간 날인 필드를 생성하는 단계 ( ... ... )





댓글 없음:
댓글 쓰기